Blog Posts
- Home /
- Blog Posts
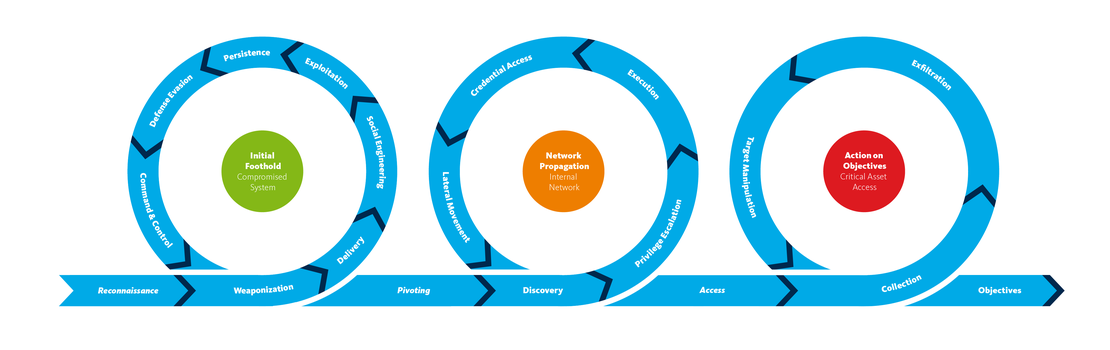
Detecting Threat Progression
The Need for Evolution in Threat Detection Cyber threats are not static; they evolve as threat actors adapt their strategies to bypass defenses.
Read More
Invisible Intruders - Unmasking the Stealthy World of Fileless Malware
In the ever-evolving landscape of cyber threats, malware continues to be a significant concern for individuals and organizations alike.
Read More