Security
- Home /
- Categories /
- Security
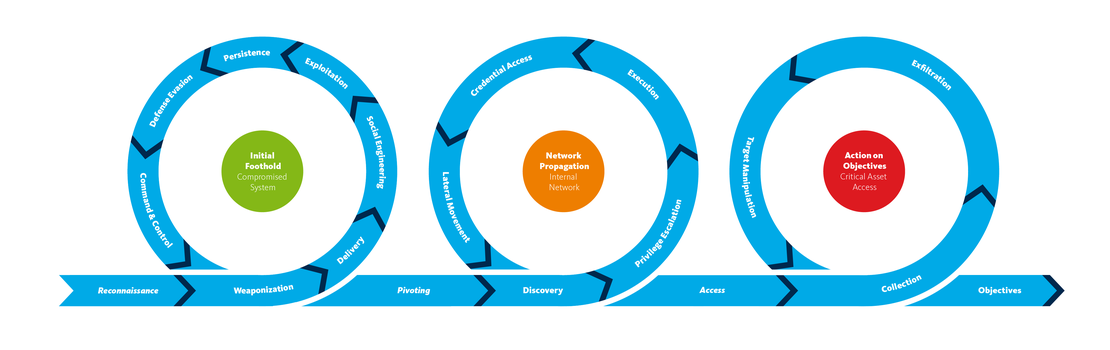
Detecting Threat Progression
The Need for Evolution in Threat Detection Cyber threats are not static; they evolve as threat actors adapt their strategies to bypass defenses.
Read More
Invisible Intruders - Unmasking the Stealthy World of Fileless Malware
In the ever-evolving landscape of cyber threats, malware continues to be a significant concern for individuals and organizations alike.
Read More
Unveiling the Secrets of Linux Core Dumps
Understanding Core Dumps: Analysis of their Purpose and Risks A Linux core dump, also known as a core dump file, is a file that captures the memory contents of a running process when it encounters a critical error or crashes.
Read More
Maximizing Threat Detection Rule Effectiveness
Maximizing Threat Detection Rule Effectiveness As security detection engineers, we constantly strive to enhance the effectiveness of our threat detection rules.
Read More